This file is used to define a system name and domain combination with a specific IP address. Linux capabilities provide a subset of the available root privileges to a process.
How To Identify The Cipher Used By An Https Connection Gsx Help Center
Check etchosts first and then look for a DNS.

. Determines the search order for look-ups usually hosts bind ie. Each of these units can then be independently be granted to processes. This effectively breaks up root privileges into smaller and distinctive units.
This file needs to always contain an entry for an IP address if the machine is connected to the network. This way the full set of privileges is reduced and decreasing the risks of exploitation.

How To Secure Your Linux Email Services With Ssl Tls Email Security Linux Email Service
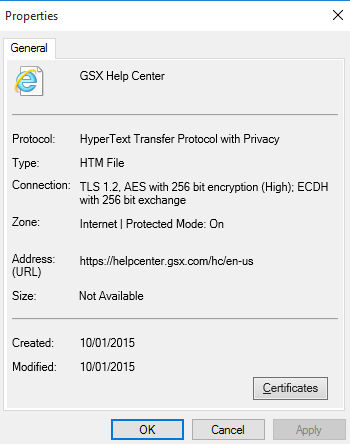
How To Identify The Cipher Used By An Https Connection Gsx Help Center

Osint Spy Search Using Osint Open Source Intelligence Best Hacking Tools Open Source Intelligence Learn Facts
0 Comments